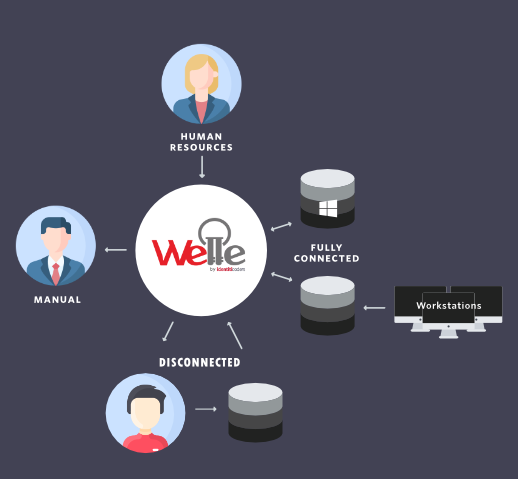
Organizations manage potentially hundreds of systems. In order
to secure each system, IT must control user access with different levels of permissions.
In a typical employee life-cycle process - hiring, role changes, resigning, permissions
on every system need to be updated frequently. This is usually through a manual process.
IC Governor automates ineffective and inefficient manual tasks to improve employee productivity,
and ensure security. It reduces the time required for audit preparation, in order to meet SLA
and regulatory compliance requirements, which are ever-changing.
If your organization is not using an IAM tool today, you are very much at risk.
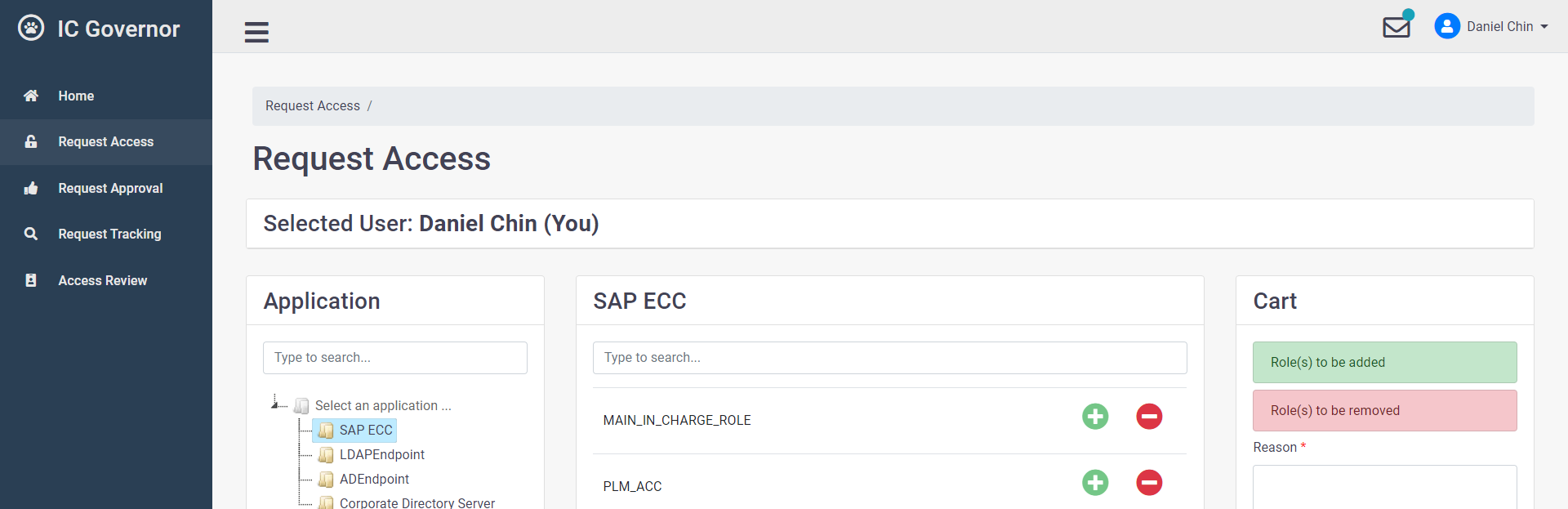
IC Governor is built with the next-generation Access Review engine in mind. It is responsive,
in terms of UX and backend remediation, and light-weight in architecture. IC Governor allows
managers to peform user access reviews and remediation of excessive access.
IC Governor provides both identity management and governance and actively audits all activities
in a centralized repository.


IT departments often use spreadsheets to track users' permissions.
Consequently, changes are missed, leaving a resigned employee gaining remote access to the network
or email system. In other times, resulting in segregation of duties issues if an employee moves to
a new department, but retains system privileges from the previous department
What's more, preparing for an external IT audit is an expensive and time-intensive process that
usually exposes loopholes that require remediation.



Essentially, IC Governor not only helps you save significant cost
and time through automation, it is most valuable in its ability to mitigate risks and improve
security.
When staff role changes, permissions are immediately and automatically updated, eliminating
any exposure to systems. Misuse of dormant administrative accounts that are still active is
prevented. System compromise through the use of vendor passwords that never expire
will never happen.
You can be certain that you are meeting regulatory compliance requirements.
We’ll partner with you to help define business requirements. We’ll conduct workshops with your application teams to identify their security concerns and automation requirements.
We will translate your business requirements and design solutions that will fulfil your needs. We might customize IC Governor if the default features are not tailored for your environment.
We will prepare the environment for initial synchronization, before performing production verification tests. We'll get your administrators and users trained prior to go live!

© Identiticoders Pte Ltd. | Privacy Policy