What Problems Does Welle Solve¶
Tip
Right Person, Right Access, Right Time
Overview¶
Provisioning¶
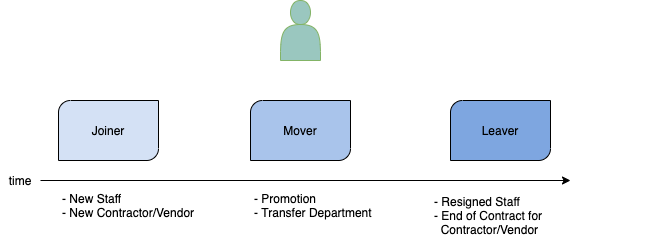
A typical life-cycle of an employee involves the Joiner, Mover and Leaver stages.
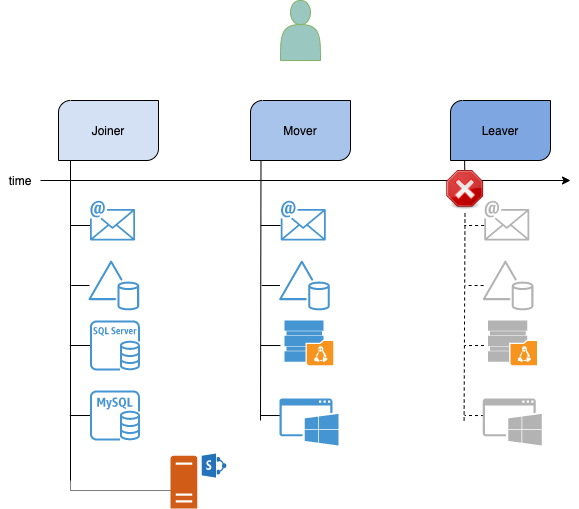
When an employee joins a company, she is granted access to Microsoft Exchange and Microsoft Active Directory. Since she is hired as a database administrator, she is also granted access to Microsoft SQL server and MySQL server.
After joining the company for a month, she needs to collaborate with her colleagues for a new project. Thus she requests access to Microsoft SharePoint. Her manager approves her access.
2 years after she started work, she changes her job scope. She is now a systems administrator.
All her previous accesses to databases and Microsoft SharePoint are revoked. Her access to Microsoft Exchange and Microsoft Active Directory remains for her day-to-day communication.
She is now granted access to Linux and Windows servers.
Finally, she decides she wants a change of environment. She quits.
On her last day, all her accesses are revoked.
The above illustration of an employee life-cycle can be automated by Identity Management software. This process is commonly known as Provisioning.
Governance¶
In most organizations, on an annual basis, IT auditors request IT departments to provide them with most recent lists of all systems and user accounts. The auditors will flag out an audit fault if any orphan or dormant account is found on any system.
Note
An Orphan Account is an account belonging to a user who has since left the organization, while a Dormant Account is an account which has not had any login activity for an extended period of time.
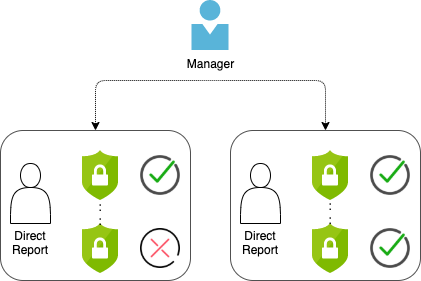
Therefore, most IT departments will require managers to perform access review on their direct reports prior to annual audit reviews.
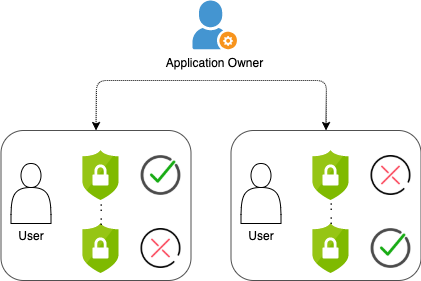
IT departments might also ask application owners to review all accounts in their applications.
Failing to perform user access reviews on a regular basis will place the organization at a higher risk for:
A resigned employee gaining remote access to the network or email system
Segregation of duties issues if an employee moves to a new department, but retains system privileges from the previous department
Misuse of dormant administrative accounts that are still active
System compromise through the use of contractor/vendor passwords that never expire
The above illustration of a user access review can be automated by Identity Governance software. This process is commonly known as Governance.
Common Pain Points¶
Ineffective and Inefficient Manual Work Orders
Repeated Process for Multiple Applications
Unable to Meet SLA and Compliance Requirements
Un-Tracked Toxic Access Combinations
Tediously Manual Compiled Access Reviews
Benefits¶
Welle is the next generation Access Review engine, which helps support enterprise IT security and regulatory compliance. You can manage the identity life-cycle in your organization in a secure and convenient portal.
Welle brings the following benefits to our customers:
Identity Management¶
Automated User Lifecycle Management
Audit and Security
User Self-Service
Identity Governance¶
To identify Orphan or Dormant Accounts
Access Review
Audit and Reports
Segregation of Duties